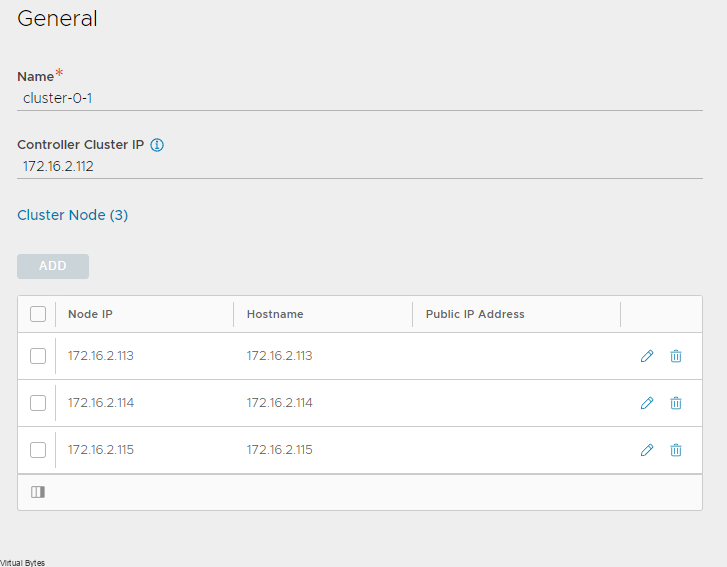
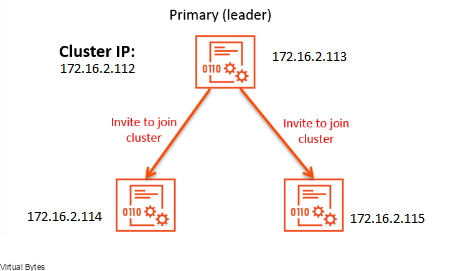
Tonight’s topic is on replacing NSX Certificate for each NSX Manager appliance and also the VIP. If you’re tired of battling with certificate issues and are looking for a straightforward solution, you’ve come to the right place! In this blog post, we will guide you through the process of replacing NSX certificates for each manager and the VIP in a hassle-free manner. We will break down the steps and provide you with expert tips to ensure a smooth transition. Let’s get started!
What you will need:
- Postman client
- Certificate CSR
- Certificate Generated by your Enterprise CA (I use Microsoft CA)
- Your Enterprise Root CA Cert
- Your newly generated Private Key
- With your admin account, log in to NSX Manager.
- Select System > Certificates.
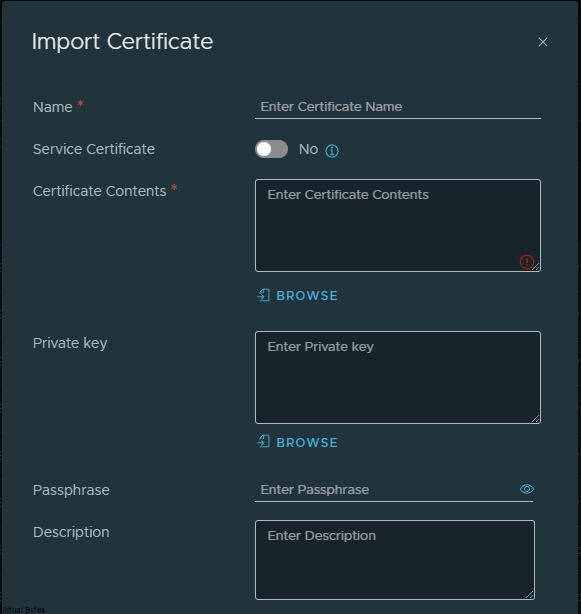
Import your Certificate and Private Key Into your NSX Manager via Web UI
Service Certificate – No
Certificate Contents
- (Cert)
- (Intermediate – if exists)
- (Root Cert)
Once you have all pre-requisites ready lets open up postman client and what you will need to do is prepare the authentication portion of your postman to authenticate successfully to the NSX Managers. Once you will then you can start getting the API calls ready.
First lets validate the certificate we imported –
GET https://<nsx-mgr>/api/v1/trust-management/certificates/<cert-id>?action=validate
https://nsx01a.prd.virtualbytes.io/api/v1/trust-management/certificates/6d78f17d-f58c-4c27-99fd-31b572dfb1e8?action=validate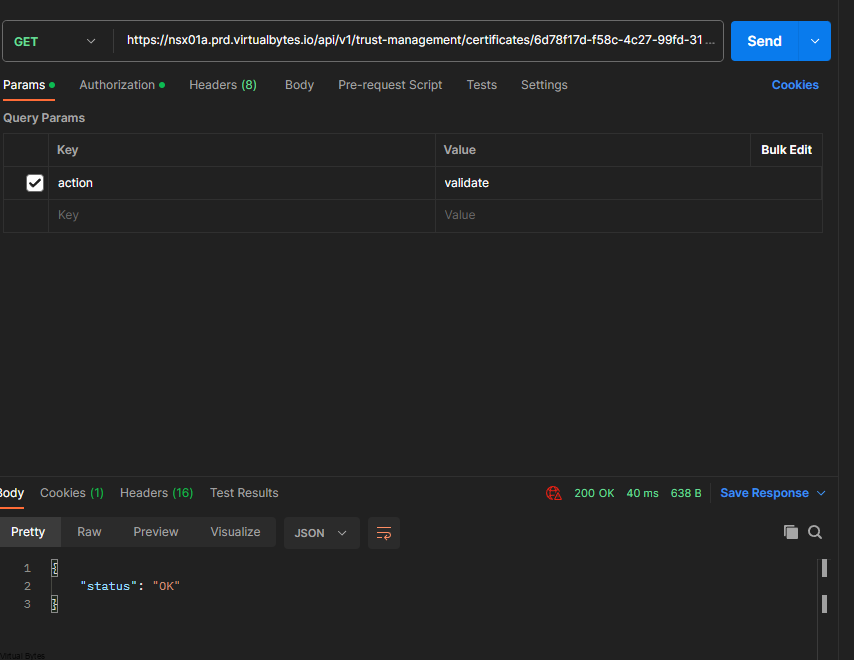
Once, you see Status OK then proceed to the next step below.
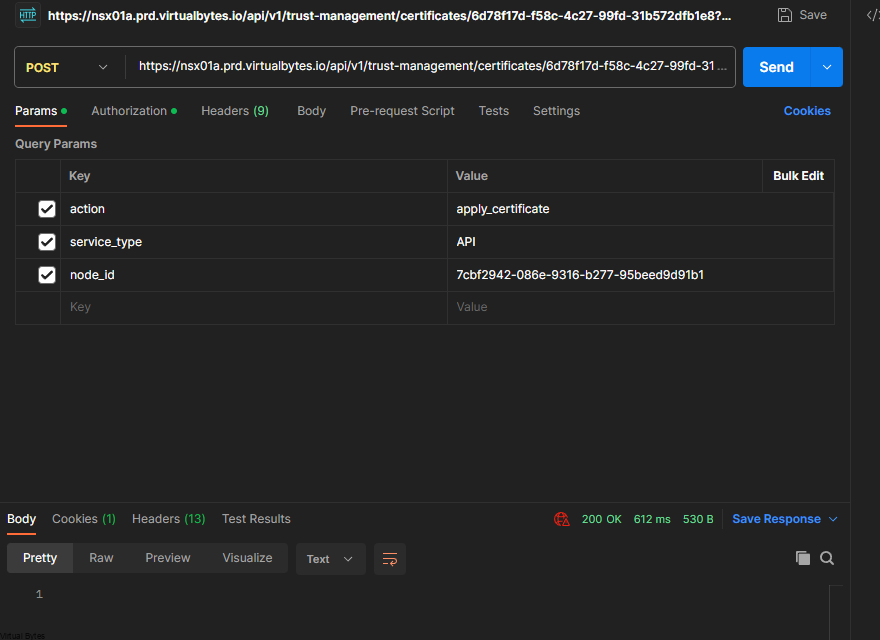
POST https://<FQDN>/api/v1/trust-management/certificates/<cert-id>?action=apply_certificate&service_type=API&node_id=<node-id>
https://nsx01a.prd.virtualbytes.io/api/v1/trust-management/certificates/6d78f17d-f58c-4c27-99fd-31b572dfb1e8?action=apply_certificate&service_type=API&node_id=7cbf2942-086e-9316-b277-95beed9d91b1Repeat the follow for the additional NSX Managers – Below you can grab the UUID from System – Appliances – UUID (Copy to Clipboard)

https://nsx01.prd.virtualbytes.io/api/v1/trust-management/certificates/6d78f17d-f58c-4c27-99fd-31b572dfb1e8?action=apply_certificate&service_type=MGMT_CLUSTER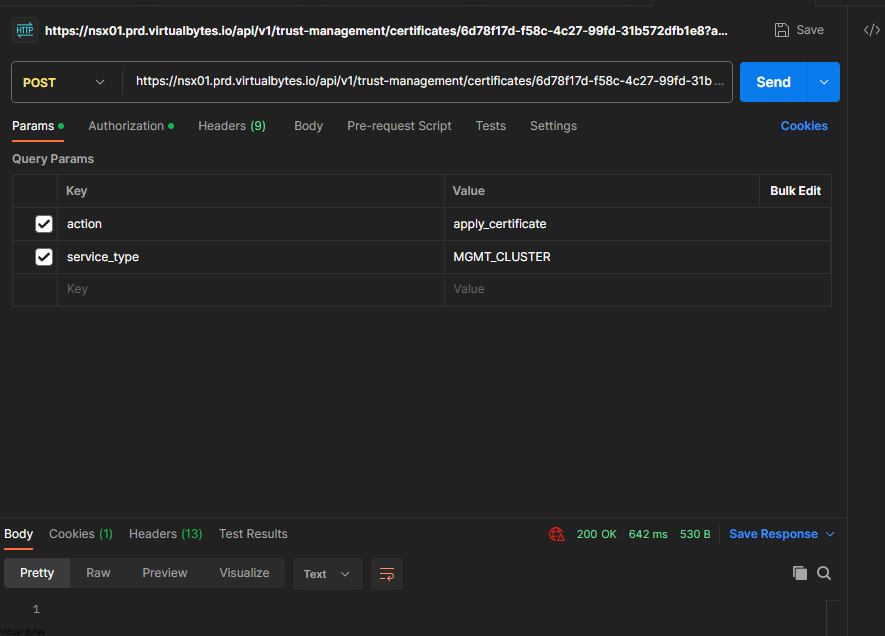
There we go, the VIP of my NSX cluster has a enterprise CA signed certificate!