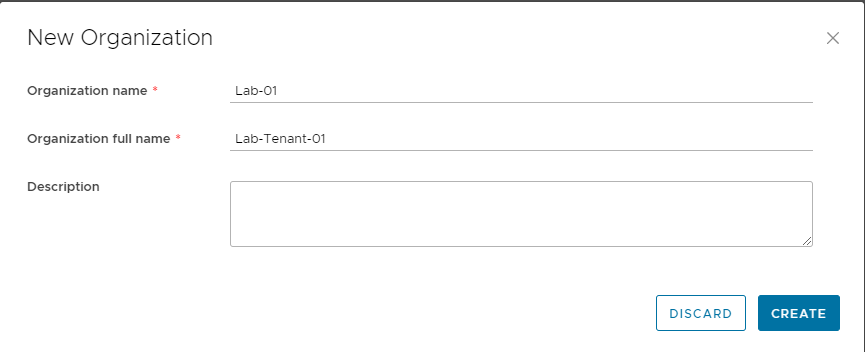
VMware has just released an exciting update Cloud Director 10.6.1—to revolutionize how we manage our cloud infrastructure. This new version is packed with powerful features designed to make IT professionals’ lives easier and their cloud services more efficient.
Cloud Director 10.6.1 offers a range of improvements, from simplifying complex tasks to providing advanced analytics. It’s all about making cloud management more accessible and effective. With this release, VMware aims to help organizations handle their hybrid cloud environments like never before.
In the following blog post, we’ll break down the exciting new features and explain how they can benefit you. Get ready to discover a streamlined approach to cloud infrastructure management!
Information from VMware’s Site Below:
Cloud computing is constantly evolving, and VMware Cloud Director (VCD) keeps advancing with new updates that strengthen security, streamline resource management, and give users greater control. VMware by Broadcom is thrilled to announce that VMware Cloud Director 10.6.1 is now available as part of the VCF (VMware Cloud Foundation) offering, starting January 31st, 2025.
Smarter VM Placement with Guest OS Awareness
Now, you can easily place virtual machines (VMs) on specific hosts or clusters based on their guest operating system. With this feature, system administrators can define VM Groups for specific OS types ensuring proper placement and compliance across all tenants. This also helps organizations stay aligned with Microsoft and other vendor licensing requirements, simplifying compliance while optimizing resource management.
Use case:
- Automatic enforcement ensures that VMs are always placed in their designated groups.
- Seamless reconfiguration means existing VMs will adopt this placement rule the next time they undergo a reconfiguration, such as a power cycle or VM edit.
This feature enhances workload distribution and simplifies multi-tenant management, giving you greater control over VM performance and security.
Take Control of API Token Security
Security is crucial and VCD now includes the ability to force API token expiration. If a token needs to be revoked immediately—whether due to security concerns or administrative changes—administrators can now invalidate it instantly. This provides a proactive approach to managing API access and securing cloud environments.
Use case:
- Instant access revocation for better security governance.
- More control for administrators over authentication and access management.
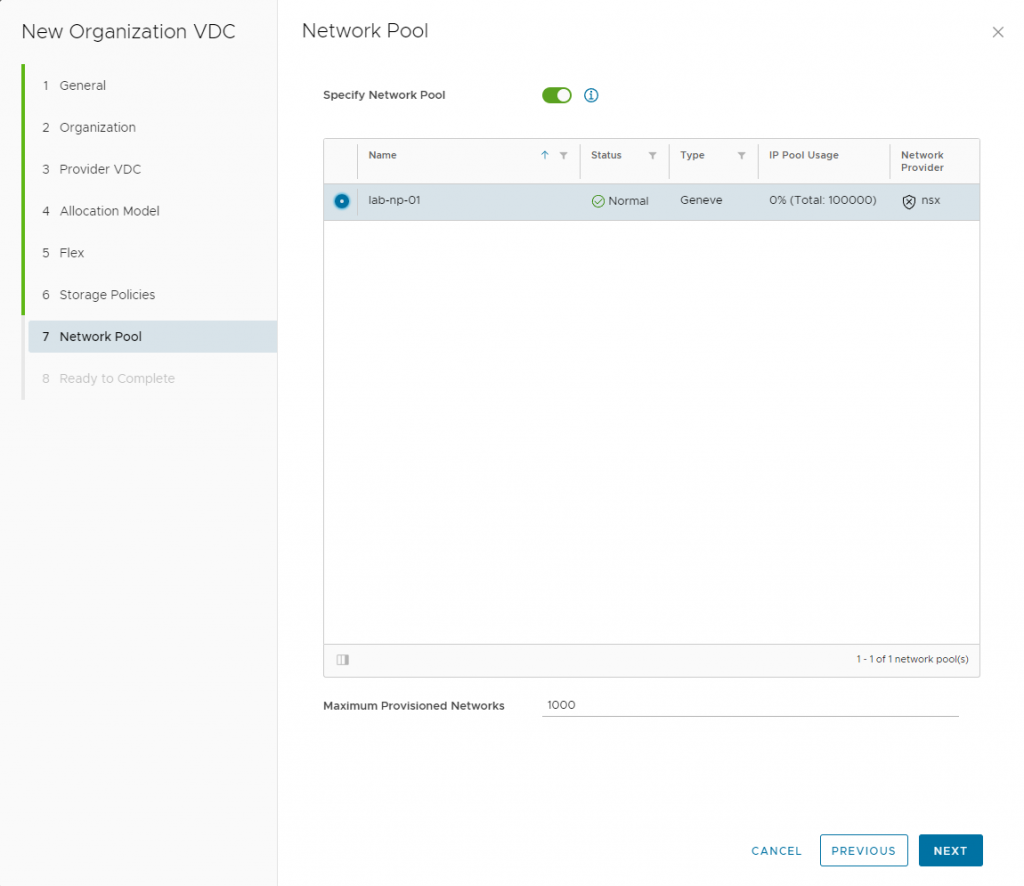
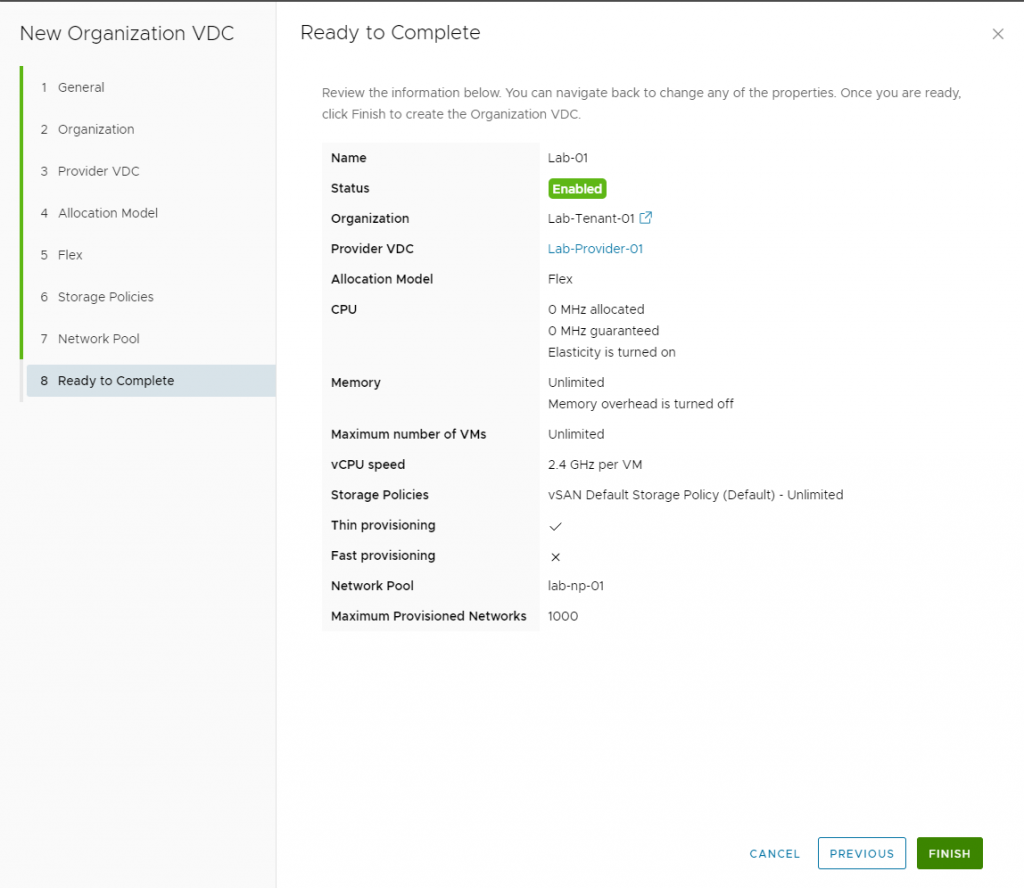
Flexible IP Retention for Sub-Providers & Managed Organizations
Managing IP addresses has never been easier! VMware Cloud Director now allows custom IP retention periods at both the sub-provider and managed organization levels. This means IP addresses can be retained even when VMs are deleted or NICs are removed—regardless of whether they were assigned via Static Pool, Static Manual, or DHCP.
Use case:
- Customizable IP retention ensures continuity and minimizes reallocation efforts.
- Metadata-based configuration allows admins to define retention periods tailored to organizational needs.
- Leverages the Manual Reservation API to preserve IPs for seamless redeployment.
No more lost IPs or unnecessary reconfigurations—just streamlined network management.
Gateway Firewall Enforcement
This update introduces the ability to explicitly activate or deactivate gateway firewall enforcement which is natively integrated within the VCF stack, with full visibility of enforcement status across T1 and T0 firewalls. Tenant and Sub-Tenant administrators both can view and override default settings, ensuring security configurations align with organizational policies.
Use case:
- Full transparency into firewall enforcement status.
- Administrative control to enable or disable enforcement as needed.
Stateful Firewall Access & Edge Cluster Configuration
Provider administrators now have improved control over the stateful firewall service, which is natively integrated within the VCF stack. With this update, they can restrict tenants from adding stateful firewall rules on T1, T0, and vApps unless the ANS security stack is entitled. Additionally, a new configuration option on edge clusters allows providers to enable or disable stateful firewalls as needed.
Use case:
- Granular control over firewall rules ensures security compliance.
- Edge cluster configuration adds another layer of flexibility in managing network security.
Custom Segment Profiles – Now Shareable!
Service providers can now share custom segment profiles with tenant organizations, making it easier to standardize networking policies across multiple tenants.
Use case:
- Improved collaboration between providers and tenants.
- Consistent networking configurations across multiple organizations.
IPv6 Transparent Load Balancing – It’s Back!
Support for IPv6 and VMware Avi Load Balancer Transparent Load Balancing is back! Pool members can now view the client’s source IP, enhancing visibility and network efficiency. To enable this feature, VMware Avi Load Balancer must be integrated with VMware Cloud Director.
Use case:
- Seamless IPv6 support for modern networking needs.
- Enhanced load balancing with transparent traffic routing.
This VMware Cloud Director update is all about greater control, improved security, and enhanced networking capabilities. Whether you’re optimizing VM placement, tightening API security, or refining firewall enforcement, these changes empower cloud providers and tenants alike.
Other Enhancements
- Fixed Update Custom Task API – No more double execution issues. The API now works correctly on the first attempt.
- Resolved All Virtual Data Centers View Issues – Admins can now seamlessly navigate the view without encountering errors.
- Removed NSX MP API References – Say goodbye to outdated NSX MP API references for a more streamlined experience.
This VMware Cloud Director update is all about better control, improved security, and enhanced networking capabilities. Whether you’re optimizing VM placement, tightening API security, or refining firewall enforcement, these changes give more control to both cloud providers and tenants.
Reference for info above: https://blogs.vmware.com/cloudprovider/2025/02/vmware-cloud-director-10-6-1-is-here-whats-new.html
Upgrade Procedure
Before we start the upgrade, lets ensure we have the following:
- Take Disk Level Snapshots of all VCD Appliances
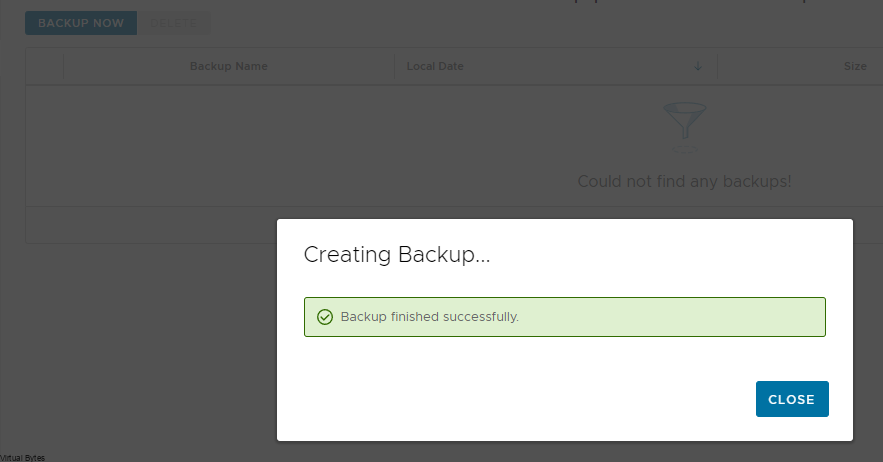
- Take Backup of VCD via VAMI
- Downloaded Bits from Broadcom’s Support Portal
My Current Version:
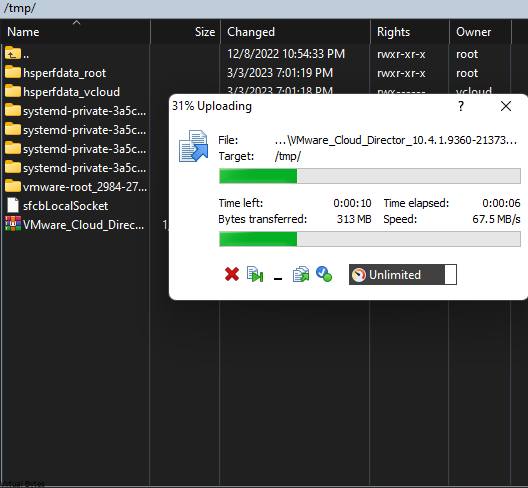
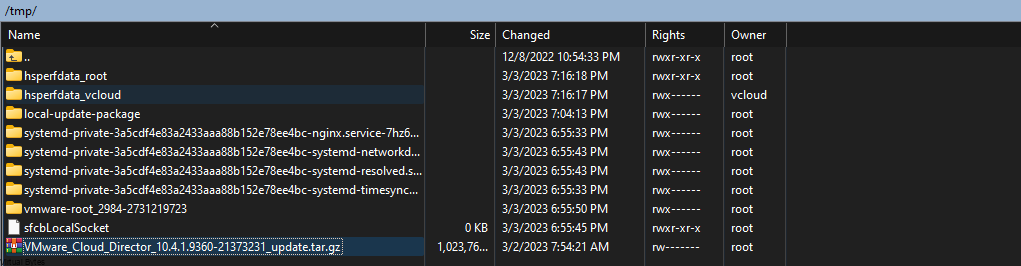
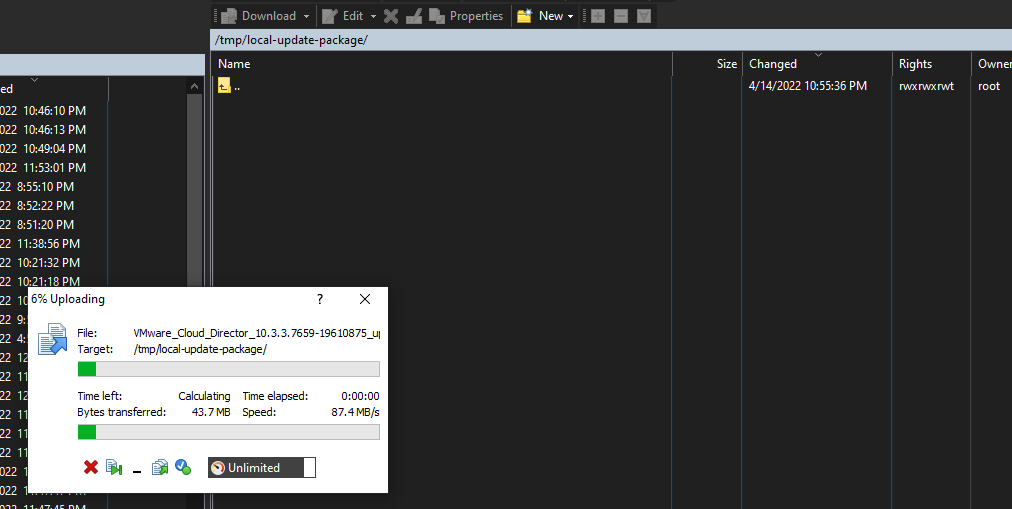
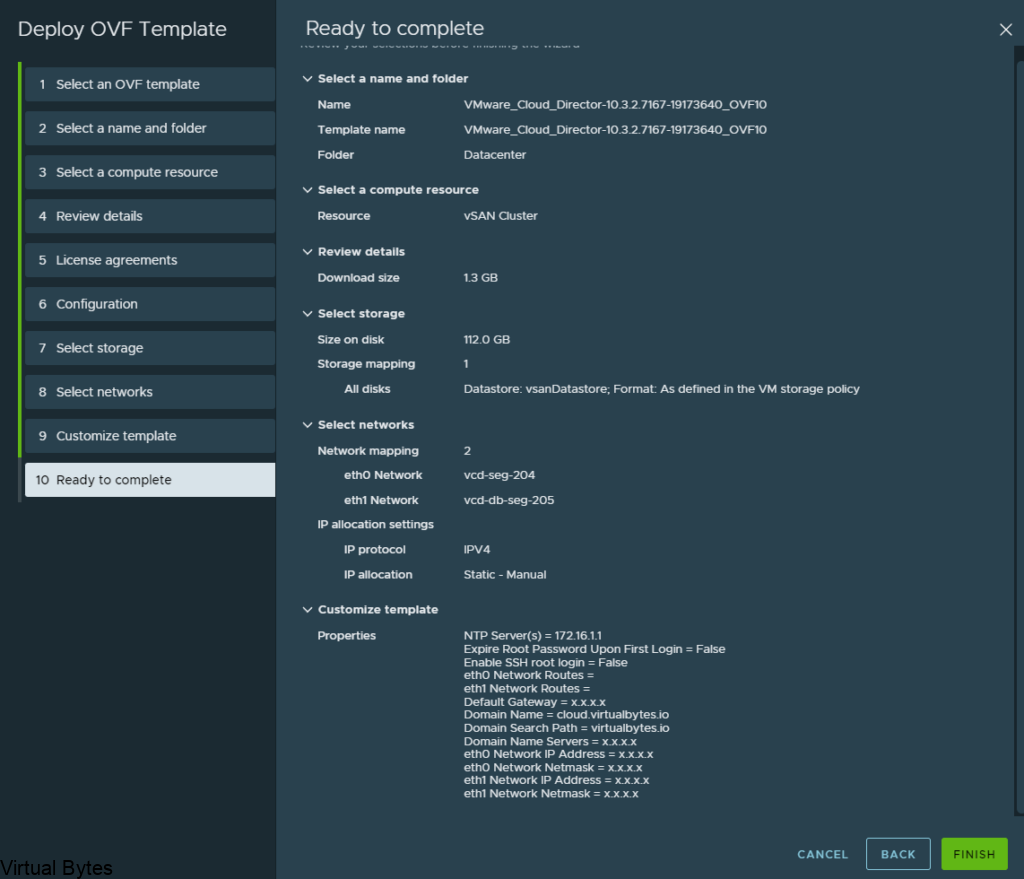
3. Upload the VMware_Cloud_Director_10.6.1.11753-24532678_update.tar.gz into the VCD appliance.
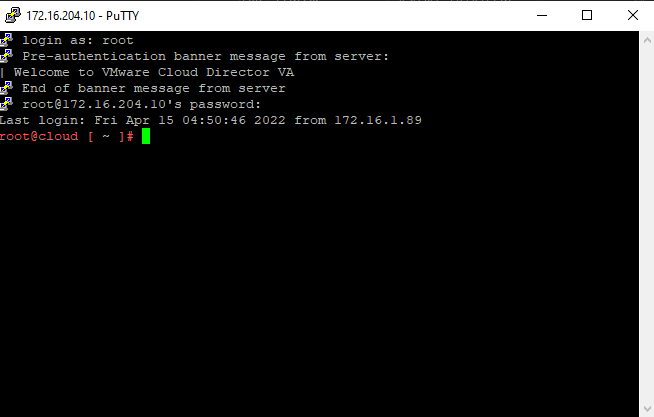
Once the update file is uploaded, SSH into the first VCD Cell appliance.
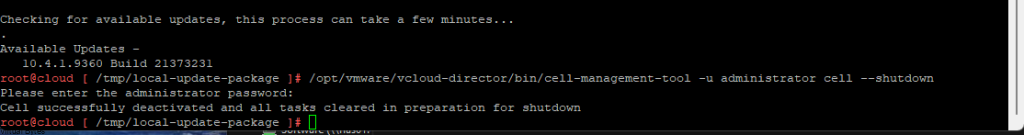
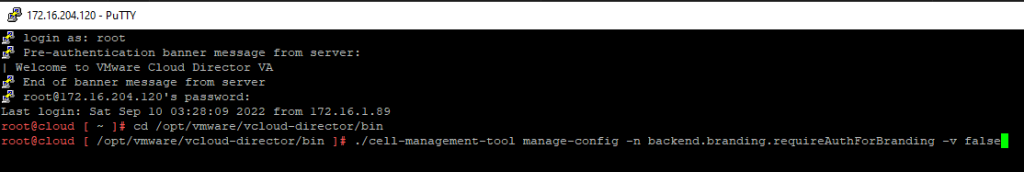
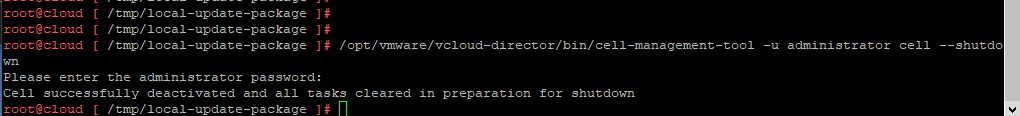
After you will need to SSH into all appliances – and you will shutdown VMware Cloud Director by running the command below:
/opt/vmware/vcloud-director/bin/cell-management-tool -u administrator cell --shutdown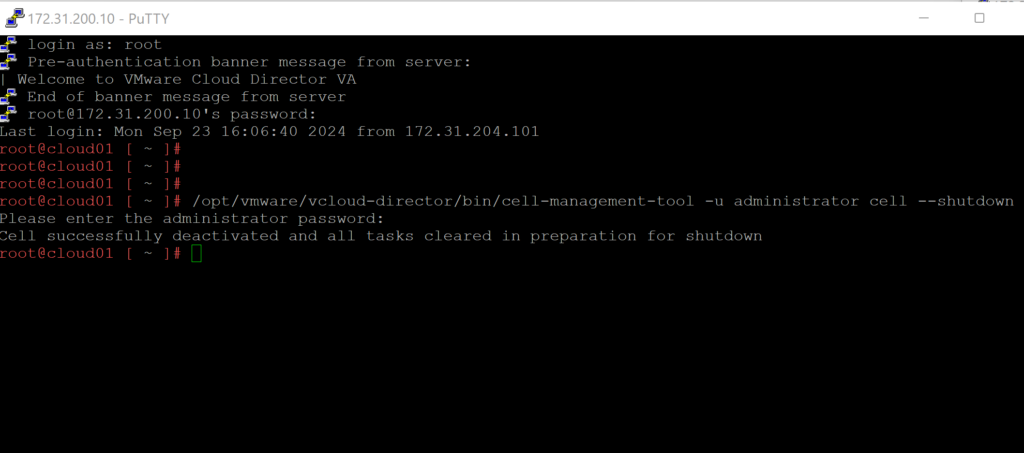
Note: It is required to upgrade the primary VCD appliance first!
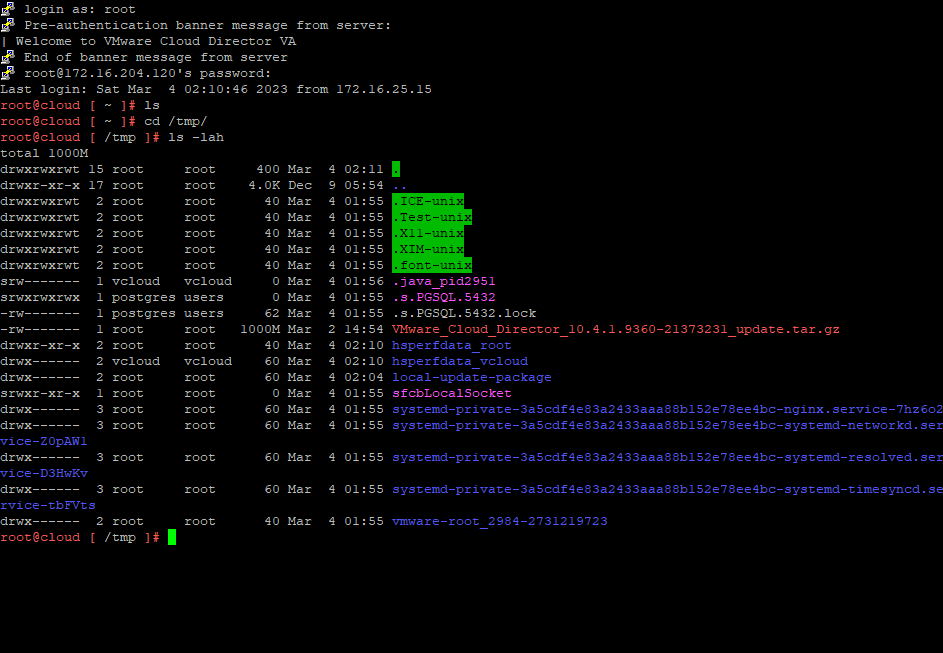
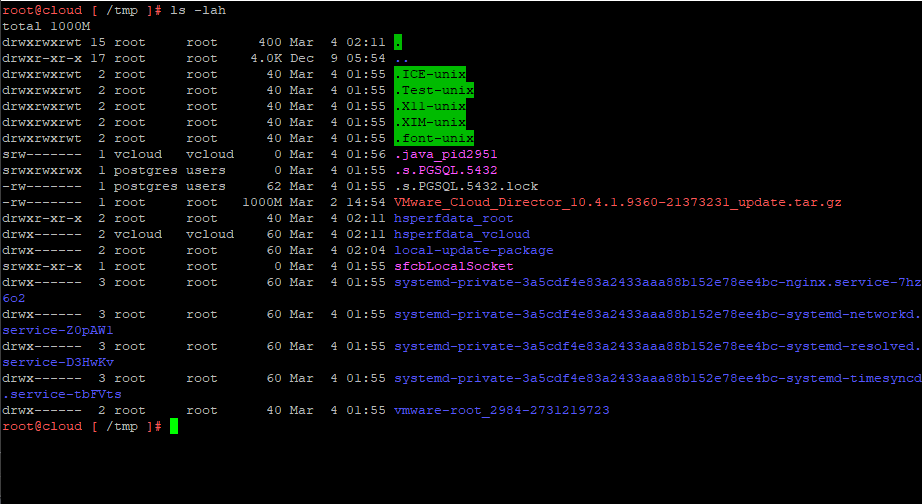
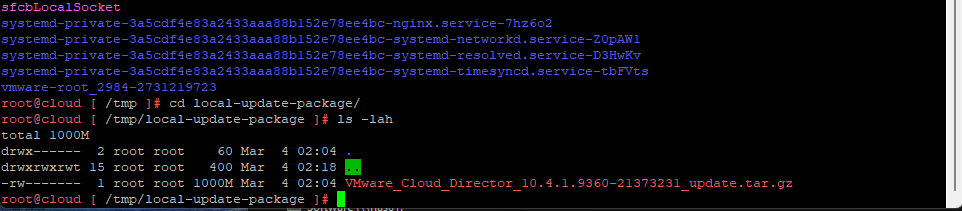
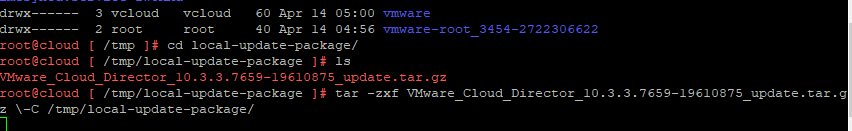
4. Lets start upgrading VCD 10.6.1 on the first appliance. Below we will un tar the Update package into the /tmp/local-update-package directory.
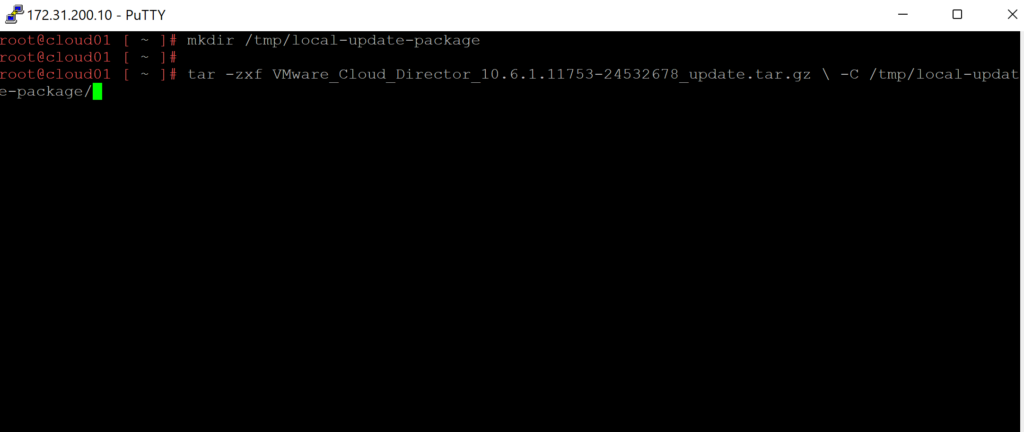
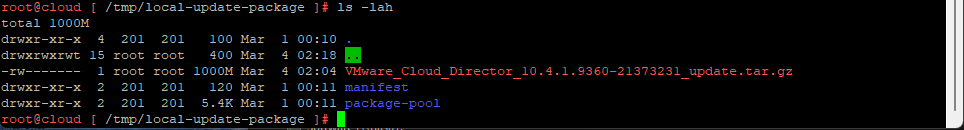
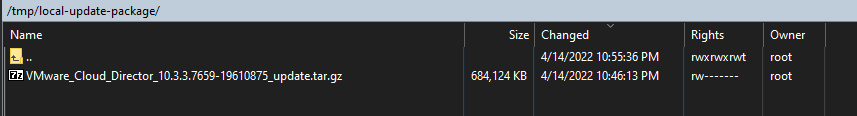
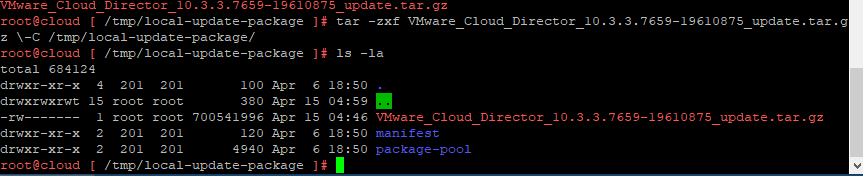
5. Let Extract the update files into the directory we created above.
tar -zxf VMware_Cloud_Director_10.6.1.11753-24532678_update.tar.gz \-C /tmp/local-update-package/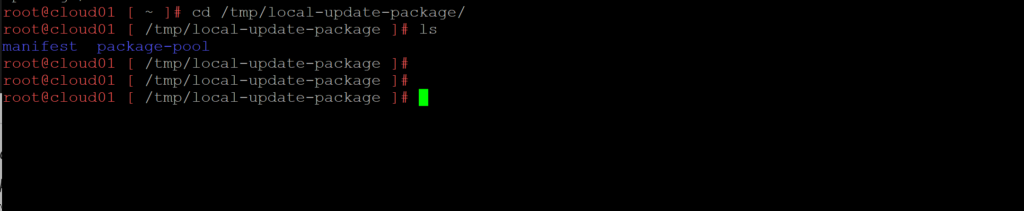
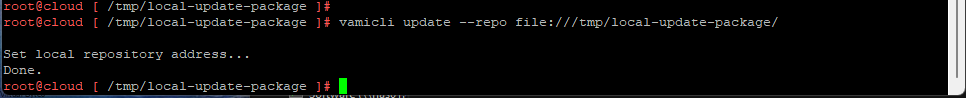
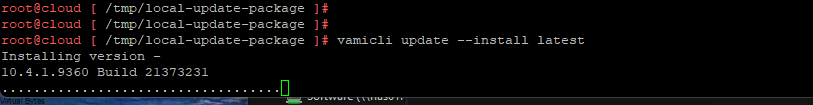
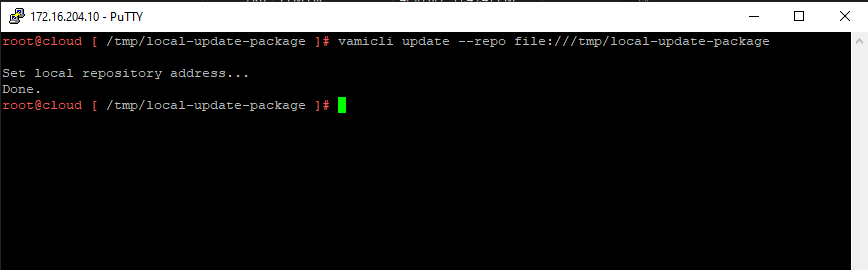
6. Now that the update package has been unzipped we will set the local-update-package be the update directory.
vamicli update --repo file:///tmp/local-update-package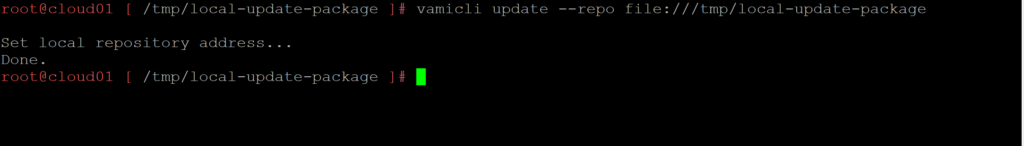
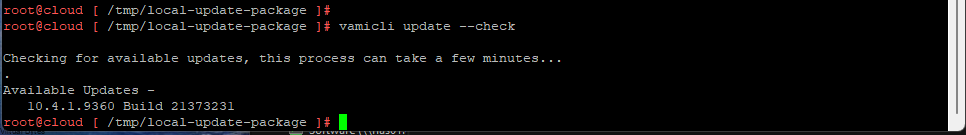
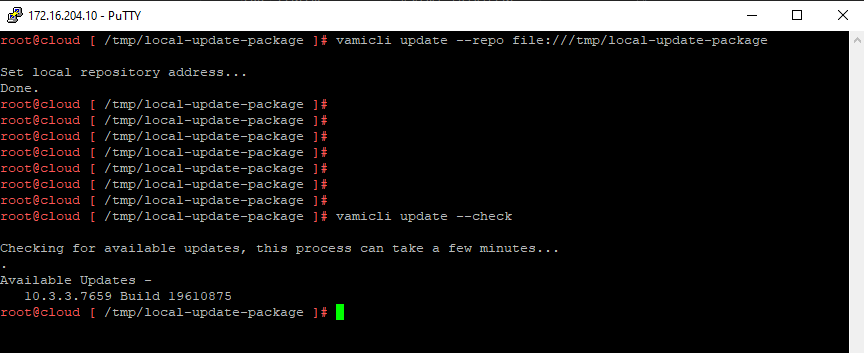
7. Using the vamicli update –check we will check the repo for the newest upgrade of VCD.
vamicli update --check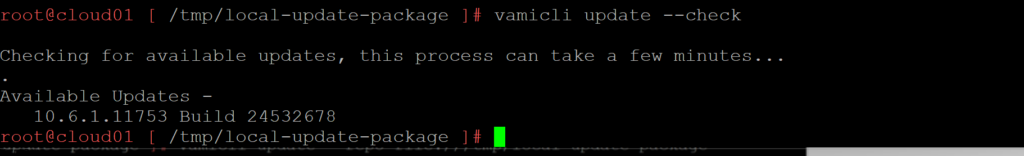
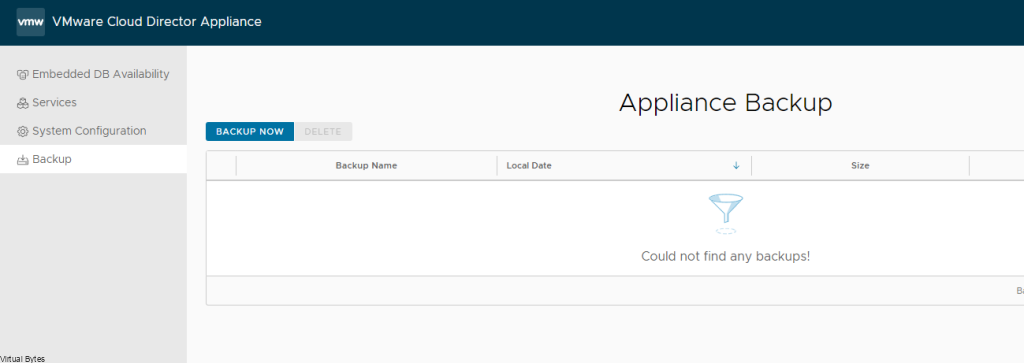
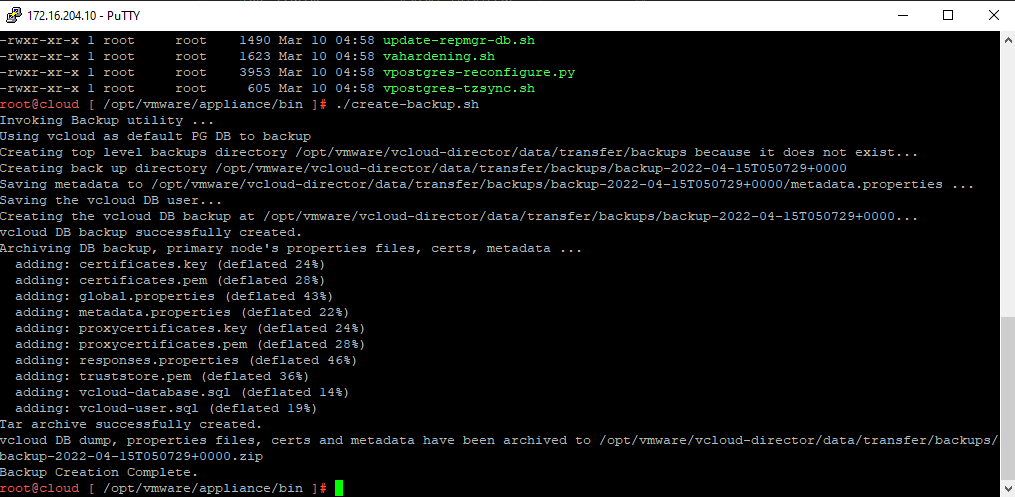
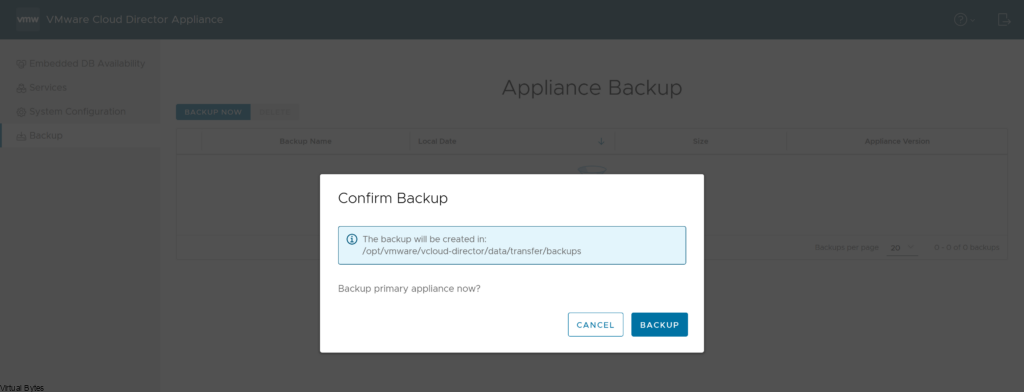
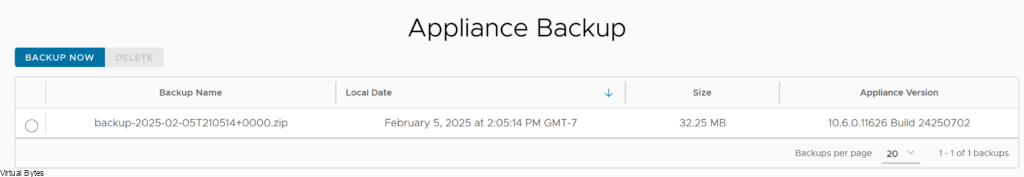
Before we start the upgrade, it is important to take a backup of the VCD Appliances, log into each VCD Node via VAMI https://IP_Address:5480 and go to Backup and take a backup.
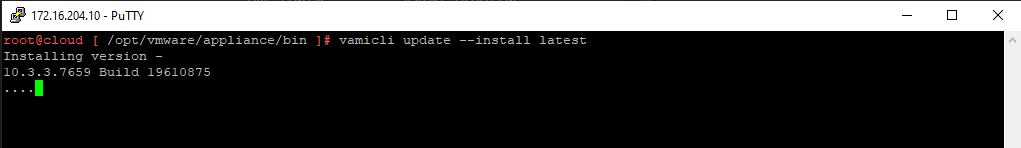
vamicli update --install latest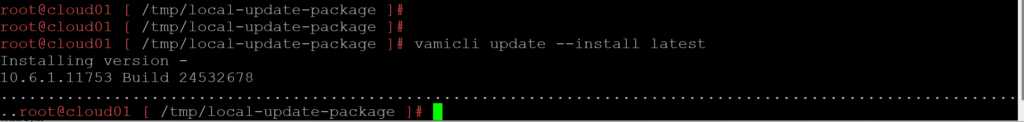
Now that the primary appliance is upgrade, repeat the steps above to the other appliances that need, steps 3 through 7.
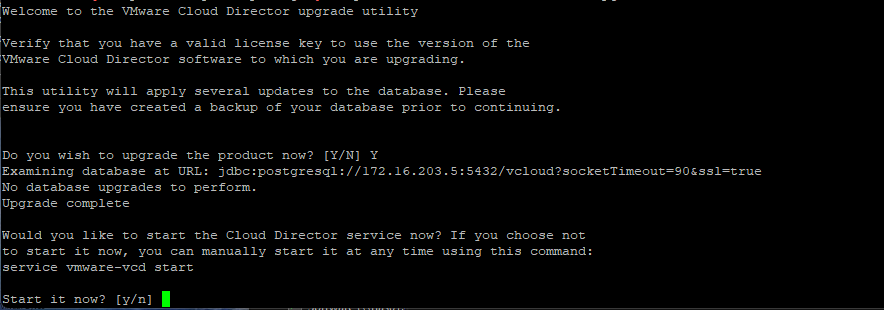
After the other VCD appliances have the upgrade staged and updated now go back to the primary appliance and execute the upgrade utility.
/opt/vmware/vcloud-director/bin/upgrade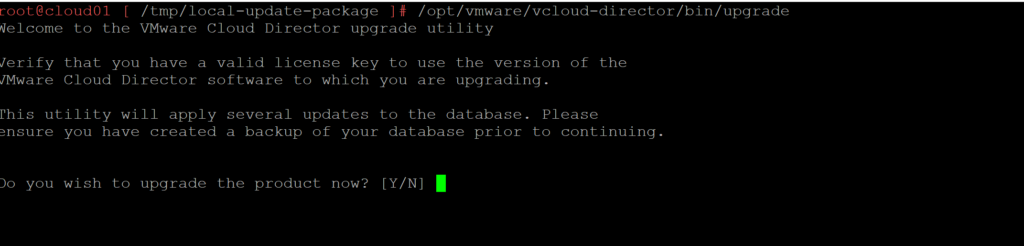
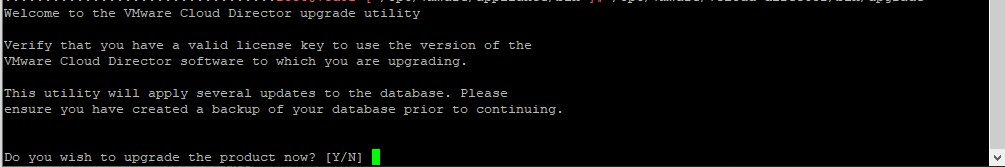
Follow the prompts from the upgrade utility, it will ask if you are ready for the upgrade and if you have taken a backup.
Once the first appliance is upgraded, then repeat the upgrade process above for the additional VCD appliances.

After the upgrade is complete, lets reboot the full appliance so for this option do No (N)
We have successfully upgraded VMware Cloud Director to 10.6.1!
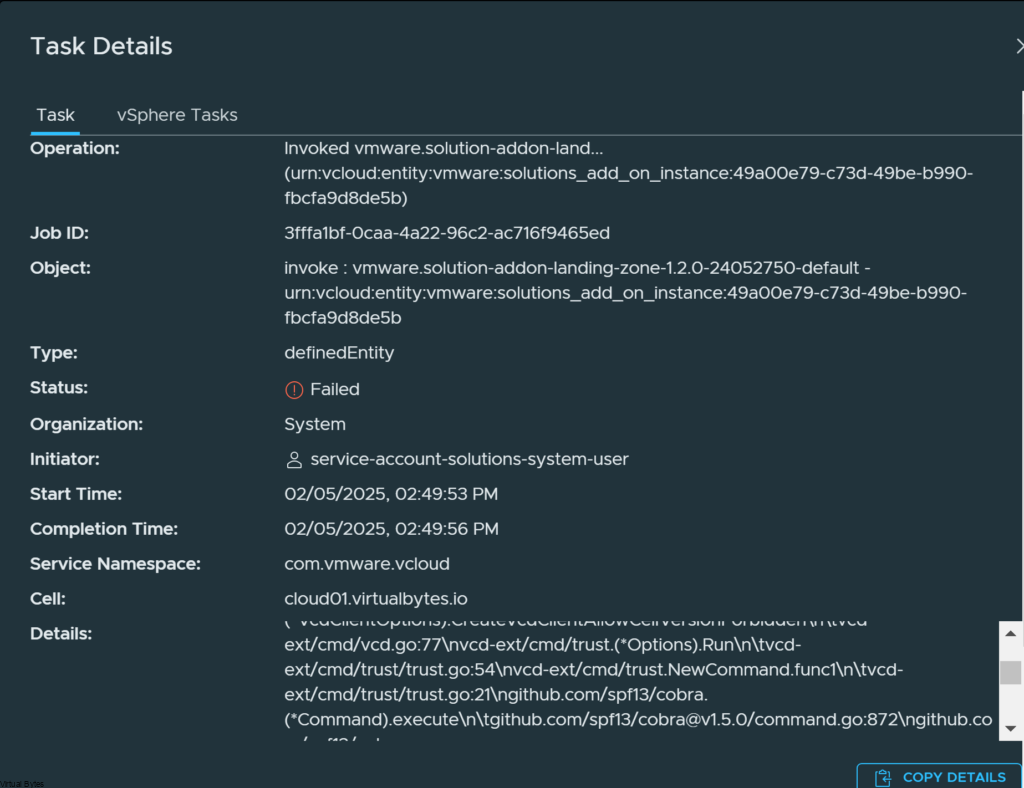
Troubleshooting After Upgrade
I logged into my VCD, first thing I noticed is that I kept getting this error:
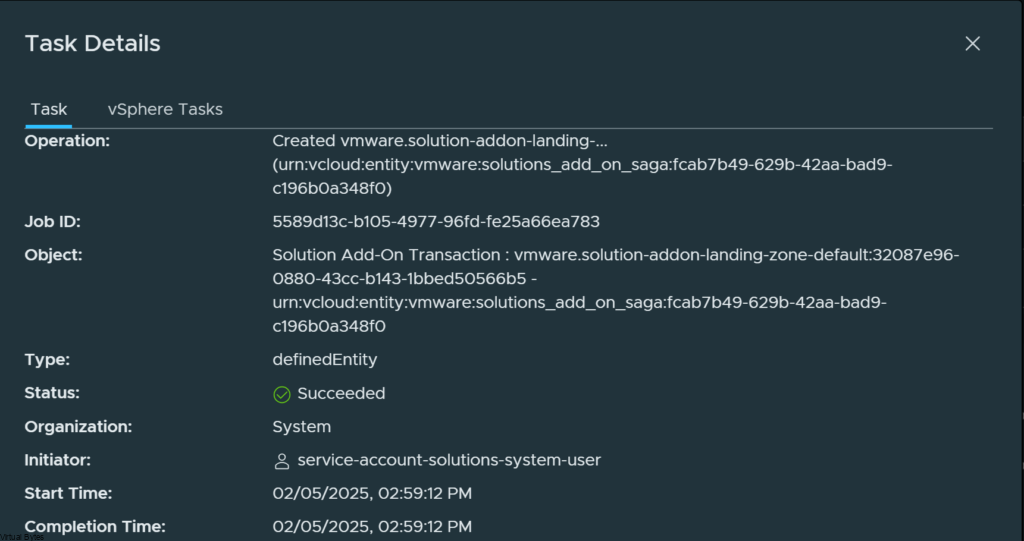
invoke : vmware.solution-addon-landing-zone-1.2.0-24052750-default – urn:vcloud:entity:vmware:solutions_add_on_instance:49a00e79-c73d-49be-b990-fbcfa9d8de5b.
Then i started looking into the issue and it was related to certificates that were expired or needed to be reapplied. After I added the new certificate the issue went away.
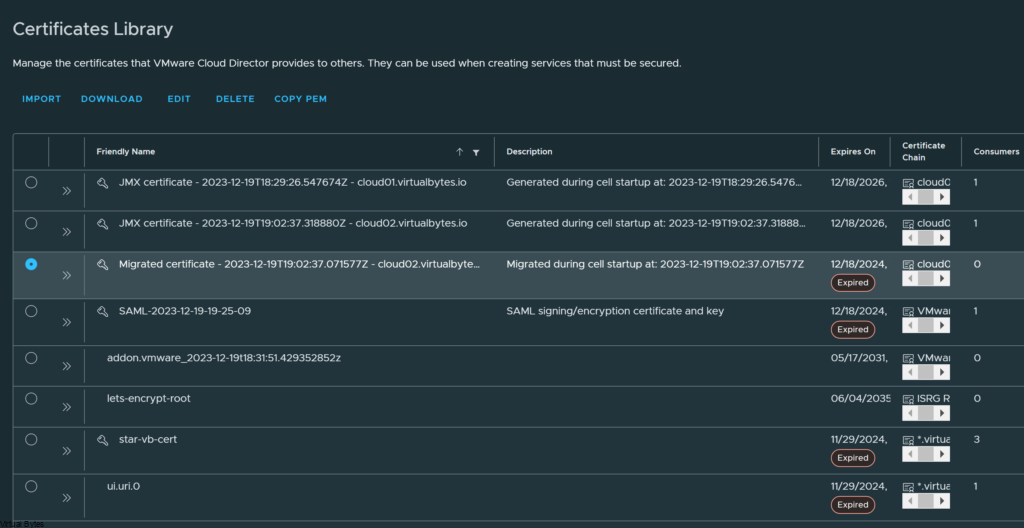
Go to Certificates Library and remove any expired certs and replace them with up-to-date ones.
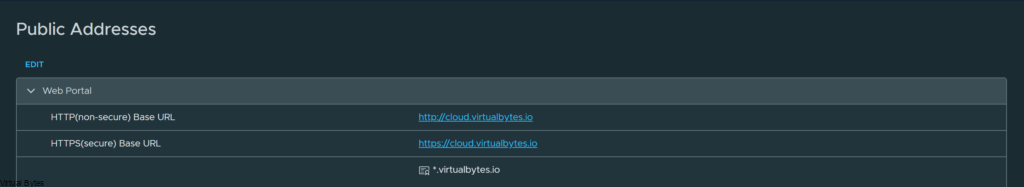
Also update the Public Addresses Certificate with the same one you uploaded into the Certificates Library if you are using a Wildcard Cert or Multiple SANs within the certificate.
Once you have all the certificates updated and cleaned up, the Task will be running automatically and here it will look like this below:
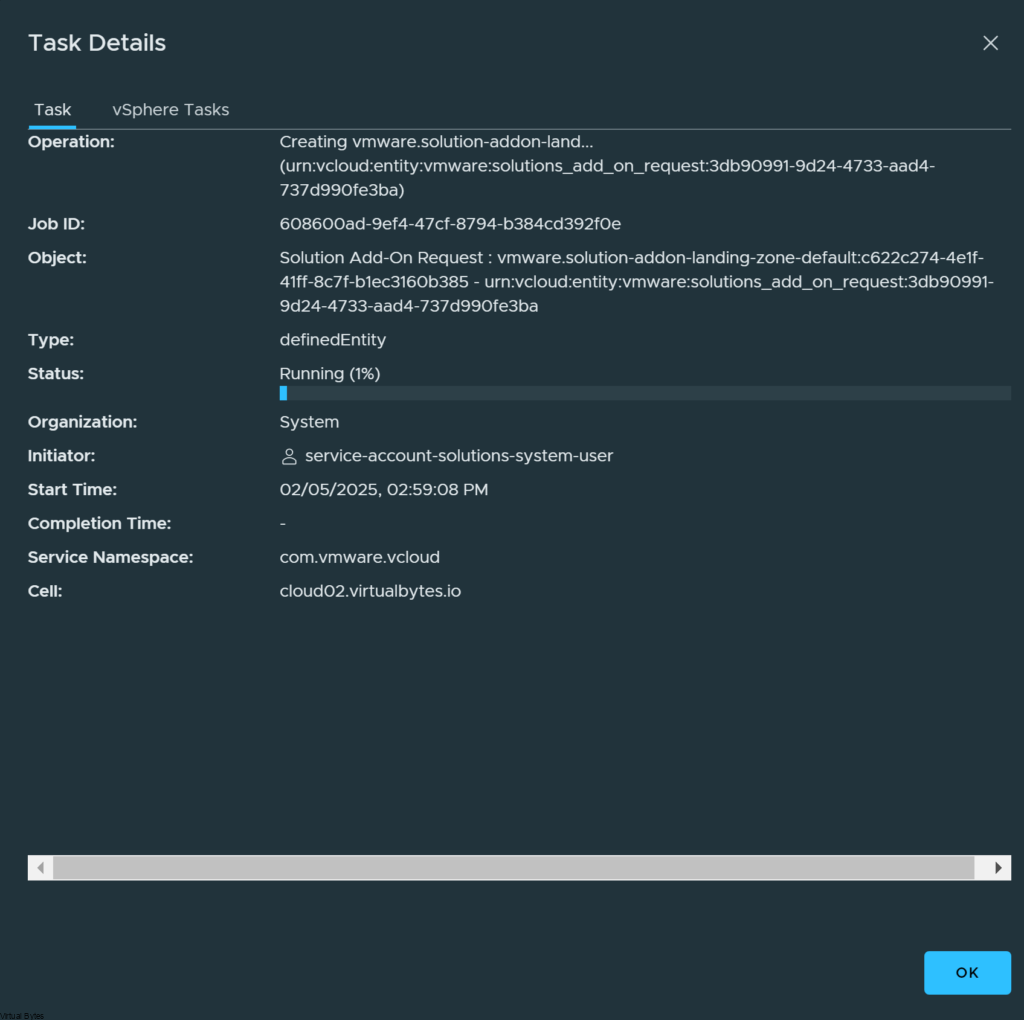
Issue Fixed!